Objective
Deploy a honeypot on an AWS server, collect data, and analyze attack methods.
Introduction
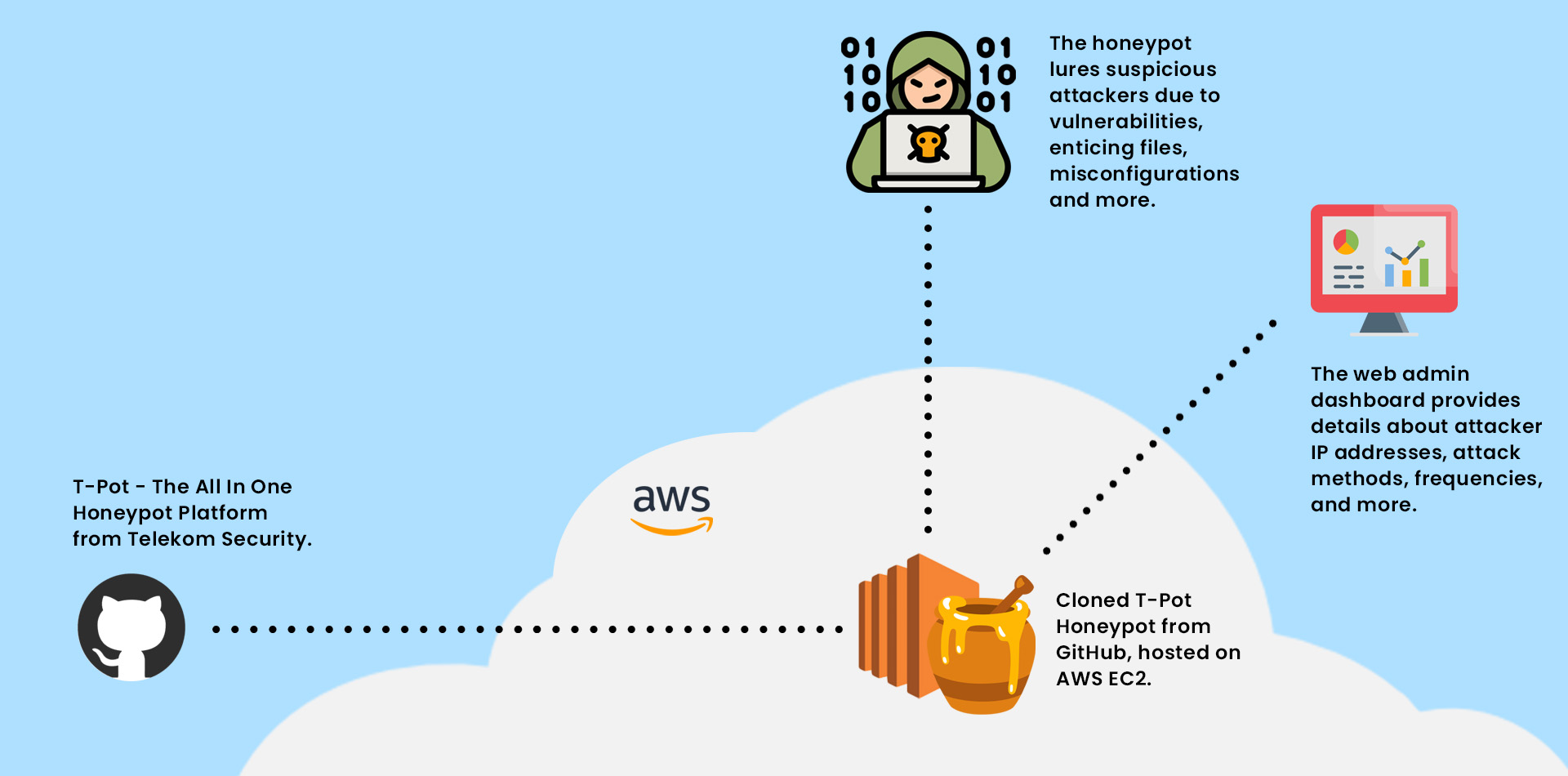
In order to gain insights into potential attack scenarios, a honeypot (T-Pot) was set up on an AWS server.
A honeypot is a cybersecurity technique where a decoy system or network is set up to attract and monitor unauthorized users and malicious activities, acting as a trap to gather information about attackers' tactics and intentions without compromising real systems or networks.
Tools & Technologies Used
AWS EC2, Inbound Rules, T-Pot (Honeypot), GitHub, Bash, Linux, SSH, VM
Implementation
1. Creation of AWS EC2 Instance:
A new AWS EC2 Instance was created with Debian 11, t3.xlarge instance type, 128 GiB gp2 storage, and a new key pair. The choice of a larger instance was made to support the ELK Stack and multiple honeypots in Docker containers.
2. Server Setup:
The server was accessed using the key pair and SSH for configuration and updates.
3. Cloning and Installation of T-Pot:
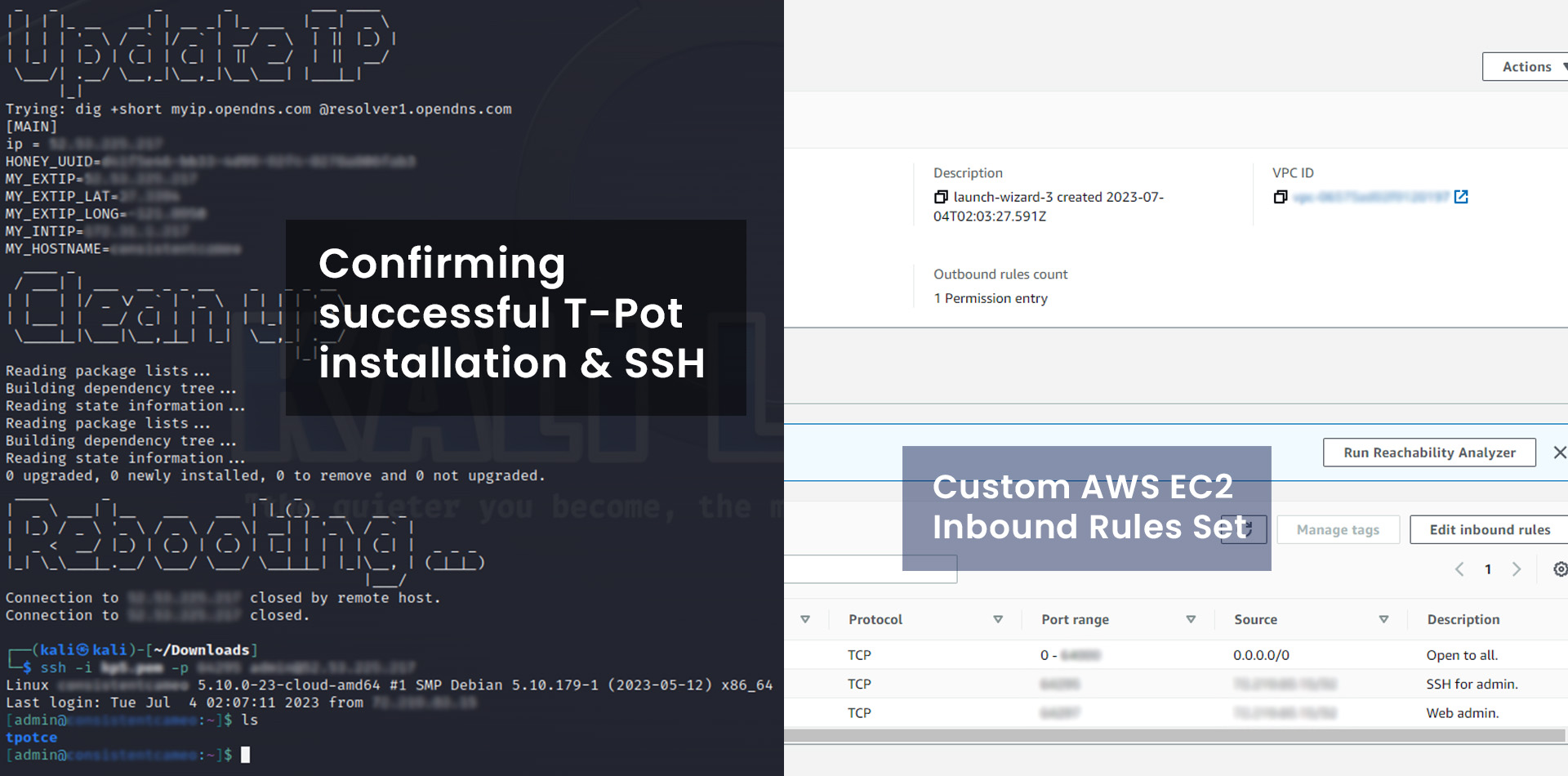
Git was installed, followed by cloning the T-Pot repository. The honeypot package was then installed, and a web user account was created for the Dashboard. After installation, the server was rebooted and reconnected to ensure successful setup.
4. Customization of Inbound Rules:
In AWS EC2 Security settings, three custom inbound rules were created to monitor incoming traffic on specific ports. One rule allowed SSH for administrative purposes, another allowed access to the web dashboard, and a third custom rule was set to allow traffic from everywhere.
5. Test the Honeypot:
After setting up the inbound rules, an SSH connection was established using the new SSH port to verify the successful installation of T-Pot on the server. The web admin portal was tested by accessing the IPV4 link with the custom port, successfully logging in, and observing incoming traffic hits.
6. Analyzing Honeypot Data:
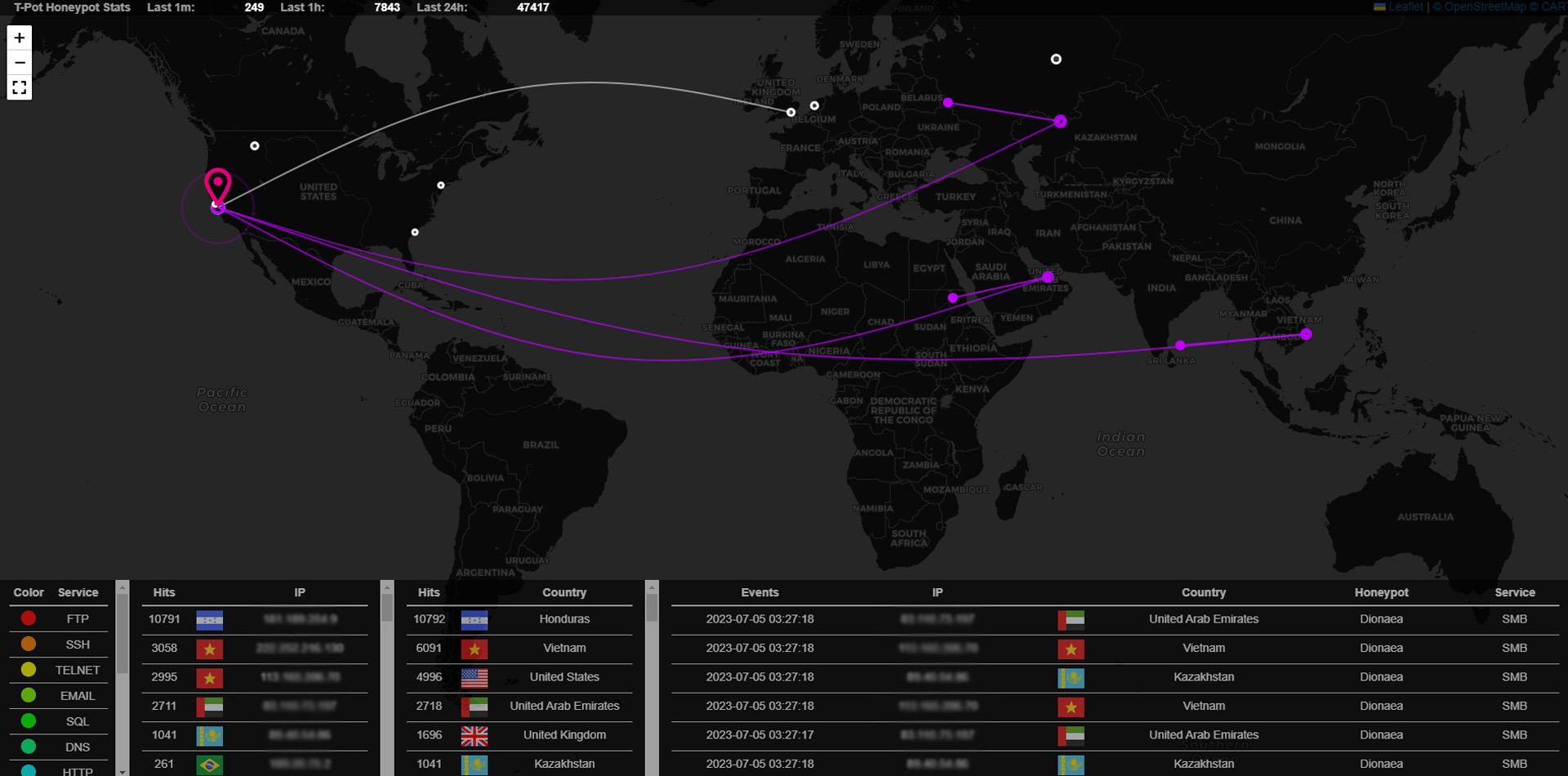
The web admin dashboard provided built-in data points to track countries, IP addresses, attack methods, frequencies, and more. Analysis of this data can help determine which IPs to block and identify services vulnerable to specific attacks.
Challenges & Lessons Learned
One challenge I encountered during the honeypot launch was determining which version of Debian to use. Initially, the instructions called for a different version, which resulted in compatibility issues when installing T-Pot. After troubleshooting and conducting online research, a different version of Debian was selected, leading to a successful setup.
Conclusion
This honeypot deployment served as an invaluable learning experience for setting up and configuring AWS EC2 servers. Additionally, it provided insights into the capabilities of T-Pot for detecting attacks.
Future plans include further analysis of collected data and the implementation of a Web Application Firewall (WAF) to block major attack types, popular Known Attacker IP addresses, and other suspicious patterns.
Data Analysis
After the honeypot was live for 10 days, I decided to analyze the data and create a WAF in AWS to block known attacker IPs and suspicious requests.


