Objective
Investigate and assess a potential phishing email I received, which appeared to be oddly tailored to my background as I actively seek cybersecurity positions, particularly as a Security Analyst.
Introduction
As a job seeker, I recently came across an email that claimed to be following up with a Security Analyst position at a company called HebeCell Corp. Initially, I was excited, but upon closer examination, I couldn't recall ever researching or applying to a biotech company. This raised red flags and prompted me to further investigate the authenticity of the email.
Tools & Technologies Used
Google, Open Source Intelligence (OSINT), Whois Lookup, Virtual Machine (VM), LinkedIn, Photoshop for the LOL's
Findings
HebeCell Corp
To start my investigation, I researched HebeCell Corp and discovered that it is a small biotech company focused on immuno-oncology and regenerative medicine based in Massachusetts. However, I was sure that I had not applied to any biotech companies, which made this connection seem suspicious.
Ben Peterson
The email was sent by someone named Ben Peterson. Curiously, I couldn't find any public connections between this person and HebeCell Corp on LinkedIn or the company's website. A Google search for "HebeCell Corp Ben Peterson" yielded no relevant results, leading me to suspect that "Ben Peterson" might be a fictitious name used in the phishing attempt.
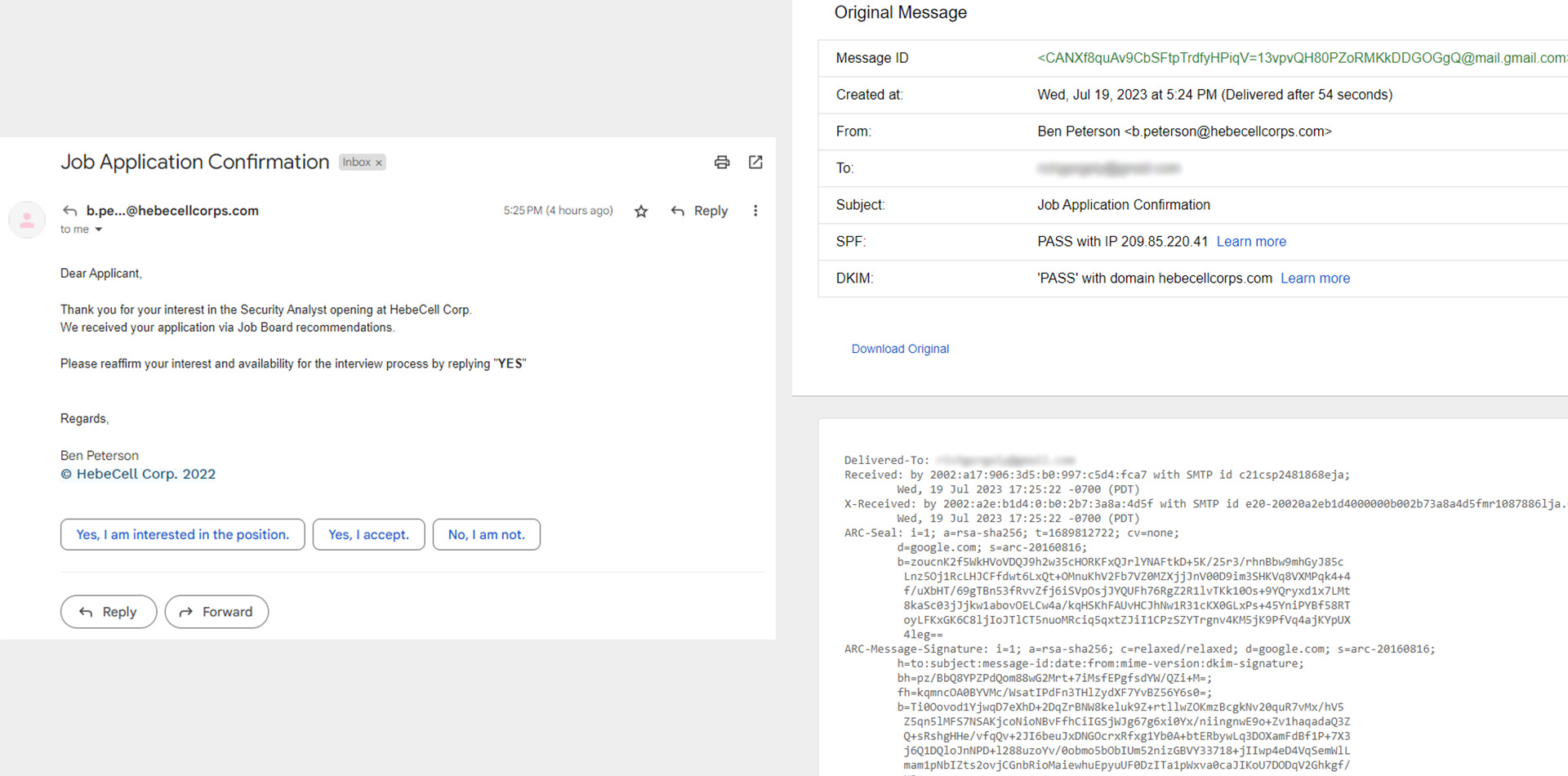
Email Address Discrepancy
I noticed that the sender's email address was "b.peterson@hebecellcorps.com," which differed slightly from the legitimate company's domain, "hebecellcorp.com." This discrepancy suggested that the sender might be trying to mimic the company's identity. I examined the email header and source code and didn't notice anything suspicious. No hidden links, the SPF and DKIM both passed, the IP was using Google Mail Server.
Asking HebeCell
I looked up the company on LinkedIn, and found a Manager who was hiring that worked at HebeCell. I asked him about this job listing & email but did not receive a response.
What Next?
To gather more insights into the phishing attempt, I decided to respond to the email with a simple "YES." In response, the sender provided an attachment labeled as a screen test with basic questions, but there was no mention of a phone or video interview, which further raised my suspicions.
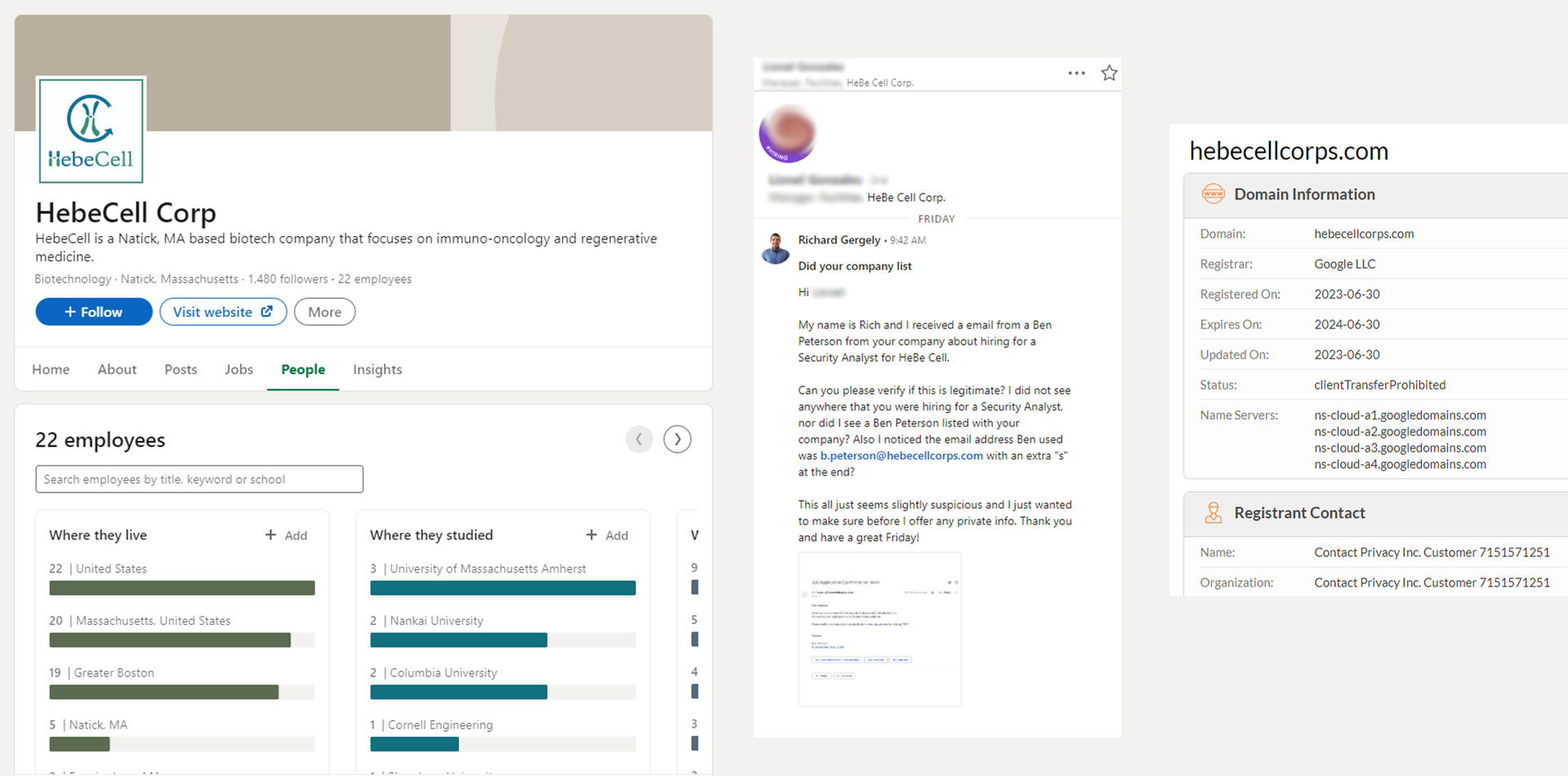
The Response
Ben responded with a screen test attachment of basic questions in an slightly unorganized word doc. There was no mention of a phone call or video interview. At this point, I am 99.9% sure this is a scam but I decide to play along and see what type of phishing scam "Ben" was trying to pull. After scanning the attachment to make sure it was not malicious, I responded to Ben that I had completed the screening and attached the same file (with no answers filled out!) in the email to see if he would say anything.
Congratulations!...
Ben responded letting me know that based on my skill and experience, I had been accepted as a new hire on with HebeCell! The next email requested my contact info to prepare the offer letter so I responded back with my "contact info." One part of the email that stood out was "Before you start, you will receive a payment(check) which will be used to set up your mini office by purchasing the office equipment and software needed"
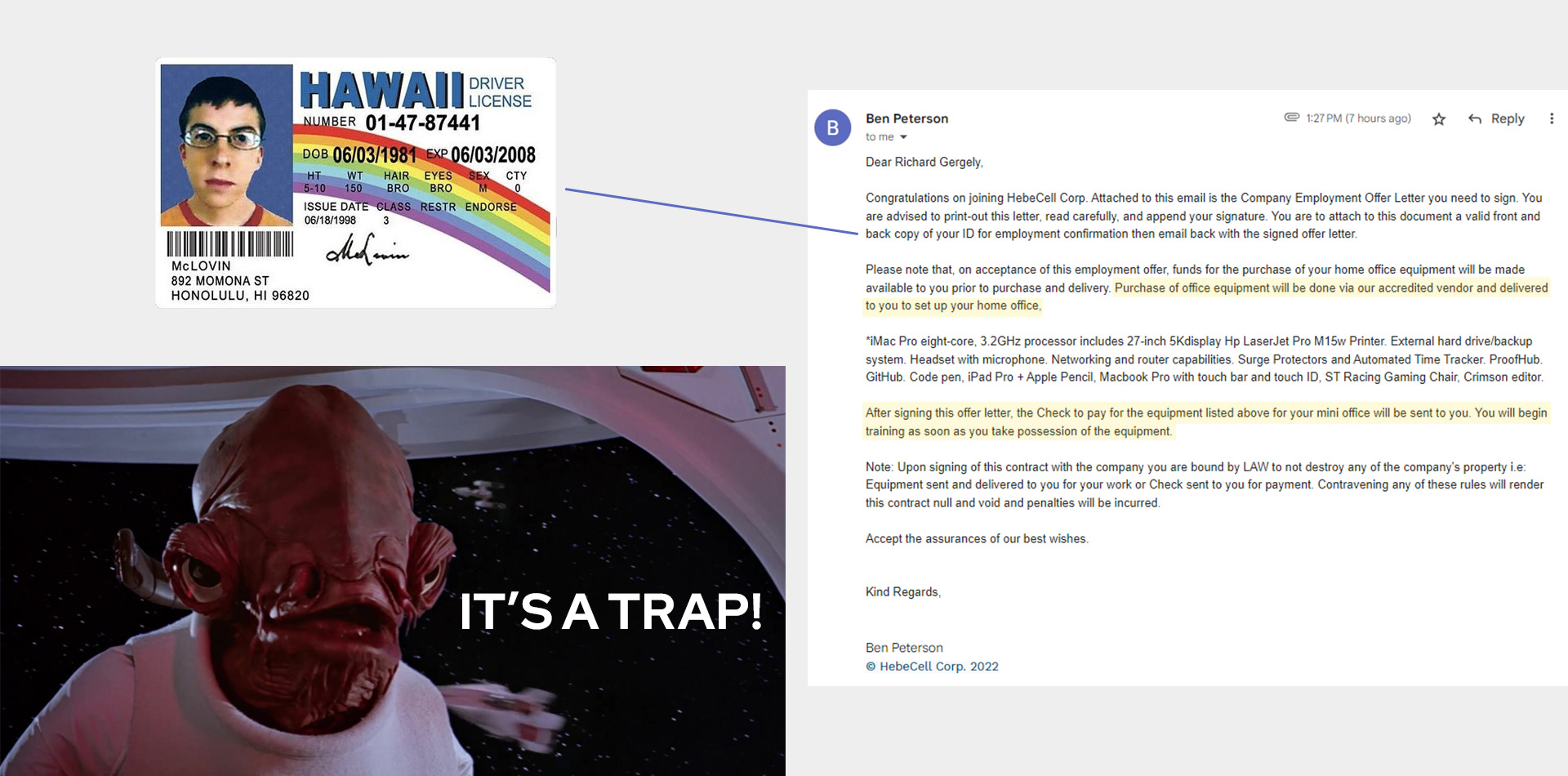
Last Response
I received an offer letter from Ben, requesting me to sign it and send back a copy of my driver's license. The email mentioned that upon completing this step, funds would be released for purchasing office equipment from their "accredited vendor." Despite the temptation to send a fake McLovin Driver's License to test their response, it became evident that this was a phishing and check scam.
The likely next step would involve them sending me a fraudulent check, which I would unknowingly deposit and use to make purchases on their "accredited link." This would enable the scammers to collect my private payment information for malicious purposes, such as identity theft, unauthorized access to my account, or making unauthorized purchases using my credit information.
Typically, my bank would detect the fraudulent check after a few days, leaving me responsible for the expenses incurred, and with no reimbursement from the fake company.
Conclusion & Lessons Learned
Based on my thorough analysis, it became evident that the email I received was, indeed, a phishing scam, attempting to exploit my interest in a Security Analyst position. The attacker utilized various tactics, including using a slightly altered email domain, an unknown identity, and the promise of a payment check.
From this experience, I learned a lot of valuable lessons:
• I need to continuously exercise caution in my email communications, verifying unknown sources and scanning attachments
• Staying informed and being vigilant about the latest phishing scams helps protect both myself and the organizations I work with
• Transforming negative experiences like this into learning opportunities showcases my dedication to continuous growth and development in the field of cybersecurity


