Objective
The objective of this project was to create a comprehensive showcase of the skills learned during the Cybersecurity Analytics Program, replicating potential challenges faced by Cybersecurity Analysts.
The entire project presentation can be viewed by clicking here.
Introduction
The project aimed to cover a wide range of cybersecurity aspects, encompassing red team and blue team methodologies, network security, incident response, threat intelligence, vulnerability assessment, risk management and more.
Tools & Technologies Used
Nmap, Hydra, SSH, Network Logging, SCP/SFTP, UFW, Iptables, Password Policy, User Management, and VM Setup.

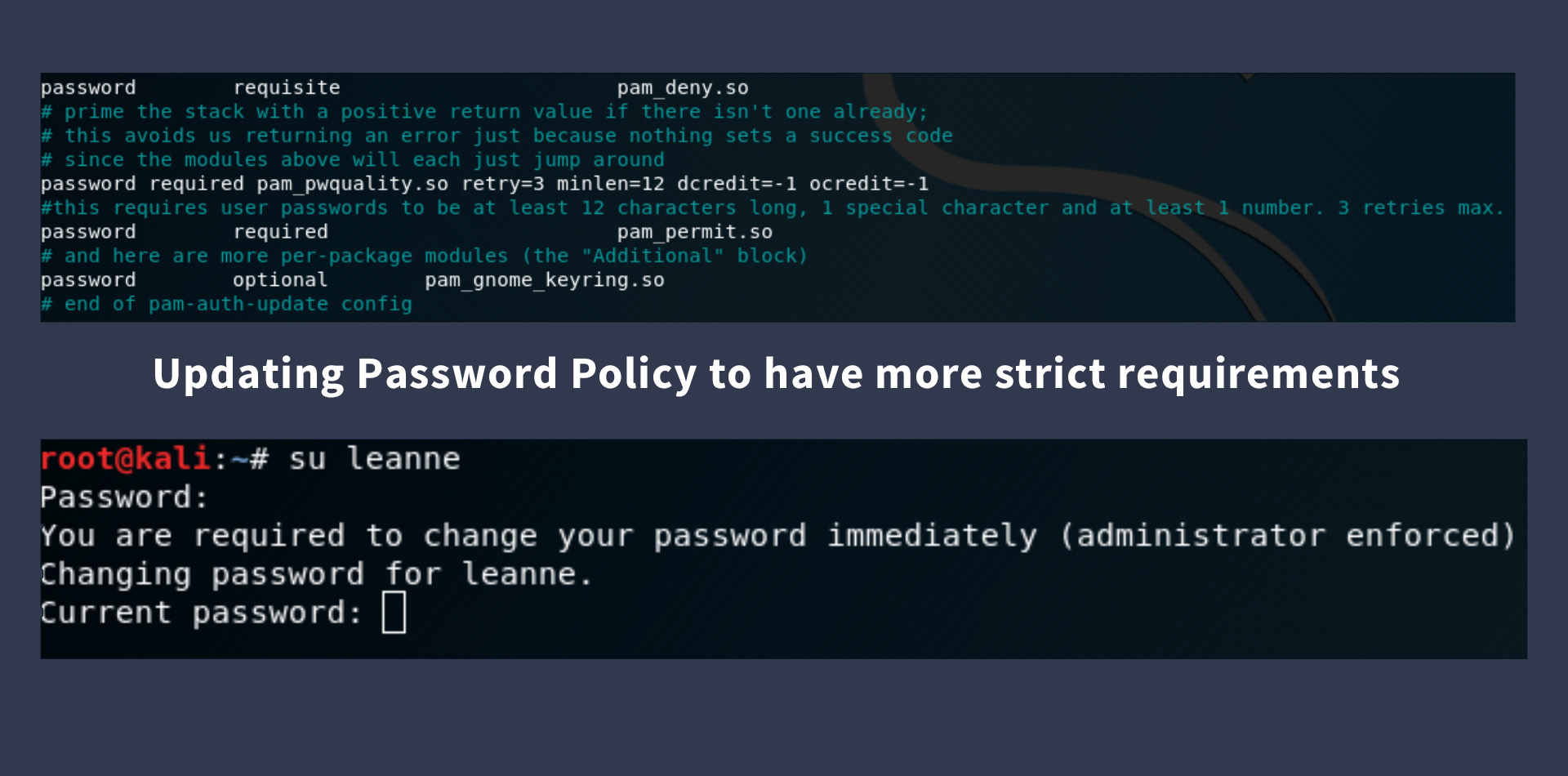
Implementation
We decided to execute a scenario simulating a Security Operations Center (SOC) team's response to a reported incident. To do this, I set up two virtual machines representing the attacker and victim systems. I planned and executed an attack on the victim, identifying vulnerabilities and compromising sensitive account information. As members of the blue team, we then analyzed and mitigated the situation, providing recommendations to prevent future attacks.
Challenges & Lessons Learned
During the project, I encountered challenges such as difficulties with intentionally using an outdated Linux VM as the victim machine. I faced hurdles while setting up and implementing SSH logging, UFW Firewalls, and other components. As a result, I decided to switch to a newer version of the Linux VM to overcome these obstacles.
By adapting and finding solutions to these challenges, I gained valuable insights and learned important lessons about the practical application of cybersecurity concepts and techniques.
Conclusion
This project successfully showcased the skills acquired during the Cybersecurity Analytics Program. We covered various cybersecurity aspects, including red team and blue team methodologies, network security, incident response, threat intelligence, vulnerability assessment and risk management.
By utilizing tools like Nmap, Hydra, SSH, and Network Logging, we simulated a Security Operations Center's response to an incident. This involved setting up virtual machines for the attacker and victim systems, executing an attack, and analyzing and mitigating the situation as the blue team. Final recommendations aimed to improve future security measures.
I gained valuable insights into the complexities of the cybersecurity field, enhancing our readiness to tackle real-world challenges as aspiring professionals.


